Yes – either over a public ip address or private ip address – depending on your scenario.
Your data will be encrypted by using a Public/Private Key Mechanism using a high-secure algorithm 256-bit Advanced Encryption Standard (AES) with symmetric keys.
The Key Pair will be generated automatically for each new customer and stored in the AWS Key Management Service.
If you decide to terminate your engagement or migrate to a different hosting environment, you can request your data of course.
We will provide you
- a compressed file for the complete data volumes encrypted with a password for download
- a compressed file with the mysql database dump encrypted with a password for download
With these data exports, your are able to setup and migrate a simplifier environment on your own.
To ensure the operation also in case of such events, we offer our Enterprise Package with High-Availability using Horizontal Scaling and 2 Data Centers akka Availability Zones to guarantee Disaster Recovery and High-Availability using more than one datacenter in more than one location/region.
By default we use data centers in germany (location frankfurt) and process all your data only within EU.
We don’t use shared resources like memory, servers etc in our simplifier cloud. Each customer gets an own tenant including all virtual networks, subnet, firewalls, servers, logs, identity management and is completed separated from other customers.
We guarantee the Service Level Agreements including Uptime for Production Environment only – The Availability differs between Hosting Models – you will find the Availability here.
We calculate the Availability in Service Health 24/7 all year long, except
- approved and agreed or planned downtimes
- nightly updates (max 15 minutes per day)
Per Default we backup daily, so the maximum loss of data from the latest Recovery Point (RPO) can be 24 hours, depending on the point of failure.
RTO, the total time for recovery, is provided via Service hours and take maximum 60 minutes.
Cloud Act is a request of accessing customer data by US Government and can only be applied if
- US Government has a legal order of punishment / warrant
- Agreement of affected Customer
In General, all request are denied. If the request is valid, there are published for full transparency.
To prevent any of your data is being accessed – simplifier cloud provides full encryption for storage, database and backups to secure your data from external access.
With each MAKERS CHOICE Release, we state all changed behaviors and migrations to be done in our Release Notes. For our Long-Term Support (LTS) Releases, we update and publish also with each MAKERS CHOICE release Pre-Release Notes providing all the information that has to be done with upgrading to the next Long-Term Support release. This allows all LTS customers to prepare for the next LTS way before it is published.
- If you have chosen the MAKERS CHOICE release option, you should upgrade to each new MAKERS CHOICE version as soon as possible, as support is only provided for the current MAKERS CHOICE release.
- For Long-Term Support releases, there is also a 3-month transition period, during which the last LTS is still supported.
Important: You decide when your instances are upgraded. If your instances are hosted in the Simplifier Cloud, simply raise a service ticket in our support portal to trigger the upgrade.
We create daily backups from database and data file volume with 7-30 days of retention, depending on the Operation Model. For more information click here.
Yes we are using two areas of data encryption.
- all Database instances, logs, backups, and snapshots are encrypted
- all File Storage Volumes are encrypted
The transport of data is encrypted either via HTTPS via TLS Version 1.2 or Web-Socket-Secure (WSS) also via TLS Version 1.2 or higher.
You will find all certificates and audits here.
We don’t own data centers or any sensitive equipment in our office location or remote locations. We operate simplifier and process your data within cloud data centers only.
All used centers are fully equipped with all the needed Equipment UPS etc. For more information about the data centers click here.
We implemented securtiy mechansim according to BSI “Grundschutz” Compendium, OWASP and ISO 27001 Guidelines. For a detailed explanation click here.
Customer data is classified within Simplifier as critical and treated accordingly, as high impact, throughout their life-cycle. We have exacting standards on how to install, service, and eventually destroy the devices when they are no longer useful. When a storage device has reached the end of its useful life, decommissions media using techniques detailed in NIST 800-88. Media that stored customer data is not removed from Simplifer control until it has been securely decommissioned.
Simplifier Cloud provides a “Shared Responsibility” divided in certain topics see picture below
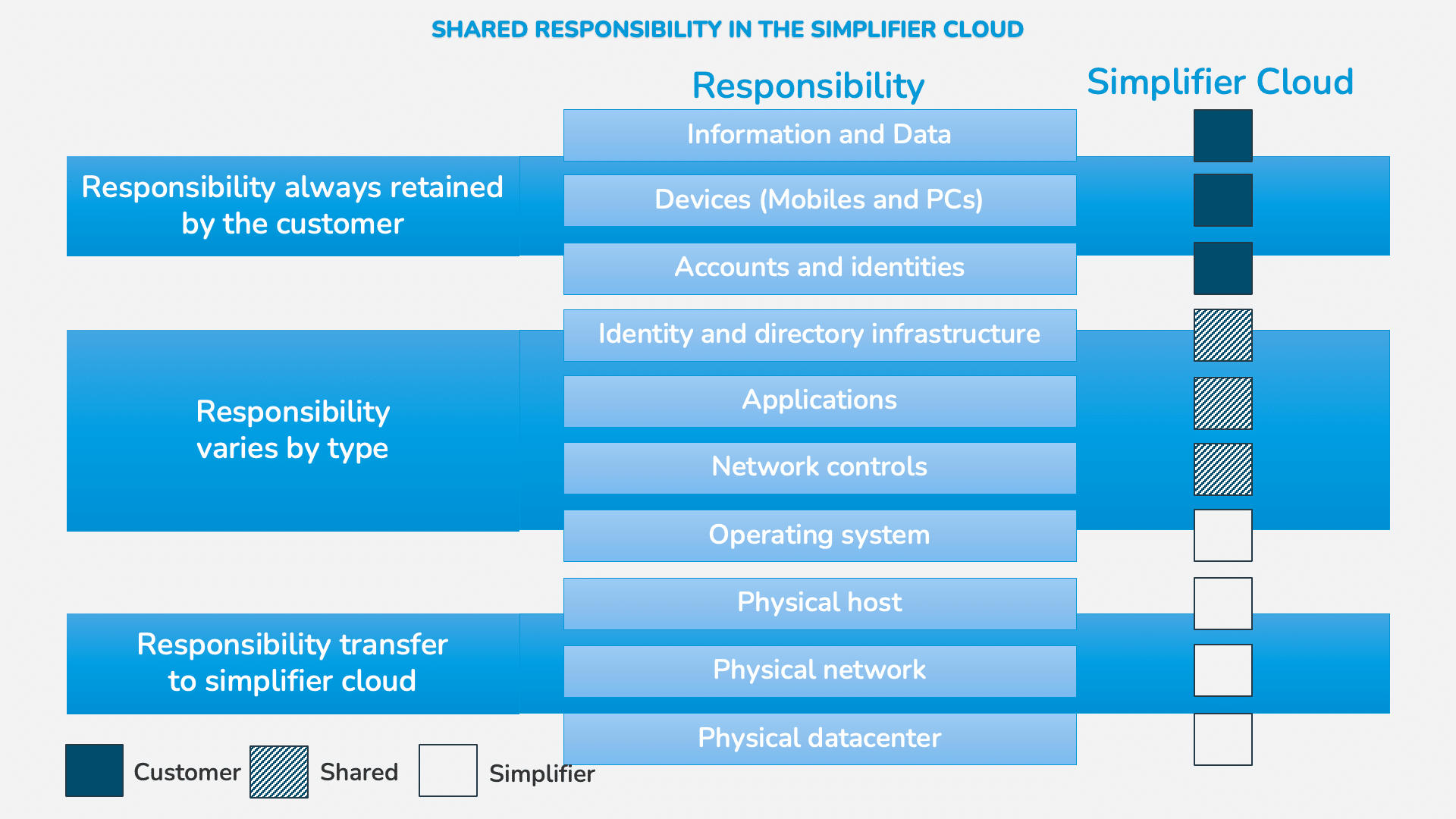
Shared Responsibilities:
Regarding the Identity Providers, Simplifier offers the ability to configure Identity Providers but the customers have to configure the endpoint on their identity provider settings.
In terms of Applications, Simplifier provides the Low-Code Platform for build and run the Customer Business Applications. The Business Applications itself are in responsibility of the customer.
Network Controls are by default configured as in our security concept, but the customer can add additional rules if necessary.











